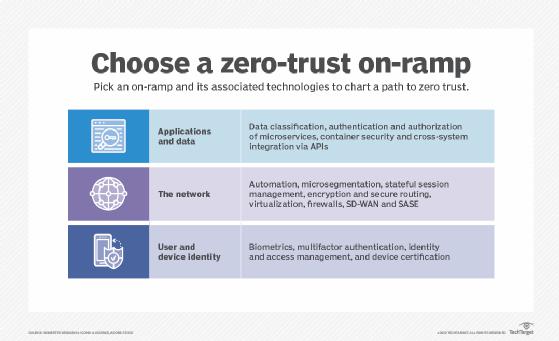
Zero trust is more than just vendors and products – it requires process
Dell Technologies World Zero-trust architectures have become a focus for enterprises trying to figure out how to secure an IT environment where data and applications are increasingly distributed outside of the traditional perimeter defenses of central datacenters.
With the attack surface expanding and cyberthreats growing in number and complexity, many organizations are sorting through a cybersecurity space that has myriad vendors and products to choose from, according to Chad Dunn, vice president for product management for Dell's Apex as-a-service business.
Zero trust – which essentially dictates that any person or device trying to access the network should not be trusted and needs to go through a strict authentication and verification process – will be foundational for companies moving forward, but it has to be more than simply buying and deploying products, Dunn told The Register in an interview here in Las Vegas at the Dell Technologies World show.
Customers have "heard of it, some of them more than others," he said. "But I don't think the awareness is where it needs to be yet.
He added: "It's one thing to have technology that is capable in a zero-trust environment. It's another to have the right processes and procedure to behave in a zero-trust model. That's the next iteration of learning. It's sort of a new discipline and it does cause you to re-examine everything from physical access to identify management to things like secure device onboarding."
Zero-trust frameworks are gaining momentum in the market. Analysts with KVB Research said the global market will hit $54.6 billion by 2026, growing an average of 18.8 percent a year until then.
The COVID-19 pandemic accelerated demand with the rapid shift to remote work, which increased risk.
In March, the Cloud Security Alliance created the Zero Trust Advancement Center led by the likes of Zscaler, CrowdStrike, and Okta to help make sense of the growing numbers of zero-trust products and approaches coming to market by establishing standards, certifications, and best practices.
Such steps could help organizations narrow their focus as they think about zero trust.
"If you ask a customer what they're doing in zero trust, they may be looking at what does this product do, what does that product do," Dunn said. "But it really involves, do you operate under the zero-trust assumption? Putting that mindset and processes in place is a much bigger thing to do. Sometimes it's easy to buy a product but harder to get an organization's processes around operating it."
Dell is putting a focus on security at the show this week, offering its Cyber Recovery Services as a full managed service in its Apex portfolio to help organizations more easily recover from ransomware and other attacks.
In addition, Dell is making data protection products available via both Amazon Web Services and Microsoft Azure, and enabling many of these to run in colocation facilities operated by the likes of Equinix, Digital Realty, and Switch.
Dell has been selling the Cyber Recovery technology to enterprises as a custom product and over the past few years has deployed more than 2,000 Cyber Recovery Vaults, which hold and protect data that can be used in case of a ransomware attack. Now it is offering it as a service.
"With security moving so quickly, the threats changing so quickly and the attack surface changing so quickly, consuming something like this as a service can be very convenient for them," Dunn said.
The company also sells its CyberSense technology for detecting incidents as well as a host of security products via its Secureworks business. Dell isn't looking to be a full cybersecurity technology provider, though it is helping organizations plan for and adopt a zero-trust model, he said.
Other vendors are also rolling out services for securing data. Hewlett Packard Enterprise in September 2021 entered the data protection-as-a-service market with disaster recovery and backup services in its GreenLake portfolio.
Many enterprises embracing zero trust are putting an emphasis on infrastructure services providers like the colocation companies, Dunn said. They give enterprises full datacenter operations, from compute and storage to connectivity, that customers don't have to manage but that are considered private, enabling them to address data privacy and sovereignty requirements.
There are also operational and managements headaches – not to mention rising costs – that come with corporate datacenters. One customer told Dunn that it would take 25 years to amortize the cost of a datacenter.
"We saw [the shift to colocation facilities] accelerate during COVID," he said. "As companies moved to a remote model, they found that they were spending a lot in real estate to house people... If you think it's expensive to house a person in an office, a rack of servers is pretty darn expensive to house.
"The way that technology is moving in terms of the power consumption and the heat dissipation because of processors – more and more usage of GPUs – it's going to get very expensive to have a datacenter. To get any reasonable density, you're going to have to start looking at things like water cooling and more and more power to each tile. Some datacenters just can't support it."
Dunn said the cybersecurity services are the first full-stack offerings in Apex and that Dell is eyeing other fields to expand such complete services into including HPC, MLOps, and virtual desktop infrastructure (VDI).
The company is also looking to expand its Apex cybersecurity services in other areas, including client systems, which will be important as hybrid working becomes the norm, which means employees working on home networks. Dunn said it's a goal he has for the second half of the year. ®
Get our Tech Resources